EUM Data Room: Confidential Document Exchange Made Simple, Efficient and Secure with Microsoft 365

It’s a use case known by millions of business professionals. Whether it’s a client exchanging their tax return with their financial planner, an entrepreneur sharing their confidential business plan with a VC, an established business submitting a performance report to a government agency, or a law firm managing an M&A, there is almost no industry that doesn’t need to share, jointly edit, and track documents.
Given the strong demand for this use case, it’s not a surprise that there are hundreds of applications available to support this exchange, ranging from options like Dropbox and Google Drive to specialized platforms tailored for specific industries or organizational needs.
Unfortunately, organizational dynamics can result in the business sourcing and utilizing these applications without involving their IT or Information Security teams. In other words, these tools are acquired by Dark IT. Also known as shadow IT, this refers to the use of unauthorized or unmanaged technologies and practices within an organization.
Dark IT poses significant cybersecurity risks. It can lead to data breaches, as employees may use unsecured applications and platforms, circumventing established security measures. Unapproved software installations can introduce malware or create vulnerabilities. Lack of oversight and control over these unauthorized practices hinders effective threat detection and incident response. Additionally, dark IT complicates compliance with data protection regulations.
But even worse than Dark IT is defaulting to sending secure documents through email. In a recent survey of business leaders in the UK, 90% of respondents indicated that they use email to communicate with their clients. More than half (55%) of respondents said that they were frustrated by not being able to find specific documents in their inbox, with 52% of them losing track of project information.
But worse than inefficiency, sending confidential documents via email introduces several cybersecurity risks. According to reports, email is a prime target for cyberattacks, including phishing, malware, and data breaches.
Research indicates that over 90% of successful cyberattacks begin with email-based phishing attempts. Email systems can be compromised, leading to unauthorized access and potential leakage of sensitive information. Inadequate encryption measures can expose documents to interception and unauthorized viewing. Additionally, human error, such as accidentally sending emails to the wrong recipients or falling victim to social engineering tactics, poses significant risks.
Secure Exchange Through Microsoft 365
Enabling secure, traceable document collaboration is an important reason that Microsoft 365 is one of the fastest growing productivity solutions in the world, with over 300 million commercial monthly active users. It’s familiar to millions of business professionals who use Excel, Word, and increasingly, Teams to complete their daily tasks. Clients managing workloads on the platform can be assured that the company has the resources to continuously update the solution and ensure best in breed security.
By making Microsoft simple, Extranet User Manager (EUM) enables each department to implement Microsoft 365 (M365) within established processes. The IT department is involved at the beginning of the deployment. They set up Delegated User Management, with administrators configuring permission structures with peace of mind knowing the permissions are set, and they are simply delegating user management to a business user that owns the relationship with their audience.
No need for Dark IT. No need to default to email.
EUM’s Data Room solution provides secure repositories that facilitate the storage, sharing, and management of sensitive information, especially in scenarios involving external stakeholders. EUM with its enriched features, unearths its proficiency in seamlessly intertwining with M365, thus moulding a reliable and user-friendly basis for creating a secure data room environment.
EUM’s Data Room solution focuses on three key aspects: security, simplicity, and flexibility to accommodate various use cases. Let’s dive into Data Room’s key features and how it ensures a holistic approach towards establishing a secure, compliant, and efficient document and data exchange with clients.
Simplicity and User-Friendly Interface
The EUM Data Room is engineered to deliver a simplified interface, contrasting with the relatively complex layout of SharePoint. This simplification aims to enhance user engagement by offering an accessible environment where both uploading and downloading of files can be achieved seamlessly. Files can be made available for download, and clients or customers can effortlessly upload files to be shared, addressing varying interaction and transactional scenarios.

Each Data Room group in the EUM Portal has an underlying SharePoint Online site. There is a two-way sync between the two interfaces, meaning any changes made on one platform will automatically sync to the other. This is optimal for version control and removing the need for duplicated efforts.
Diverse Use-Case Support
EUM’s Data Room supports multiple use cases, one of which involves an upload scenario where external parties, such as clients or customers, can upload files to be shared with the host organization. The document exchange tool is crafted to ensure the interface remains straightforward and remarkably easy to navigate, even for users who might not be technically adept.
Document Management and Tracking
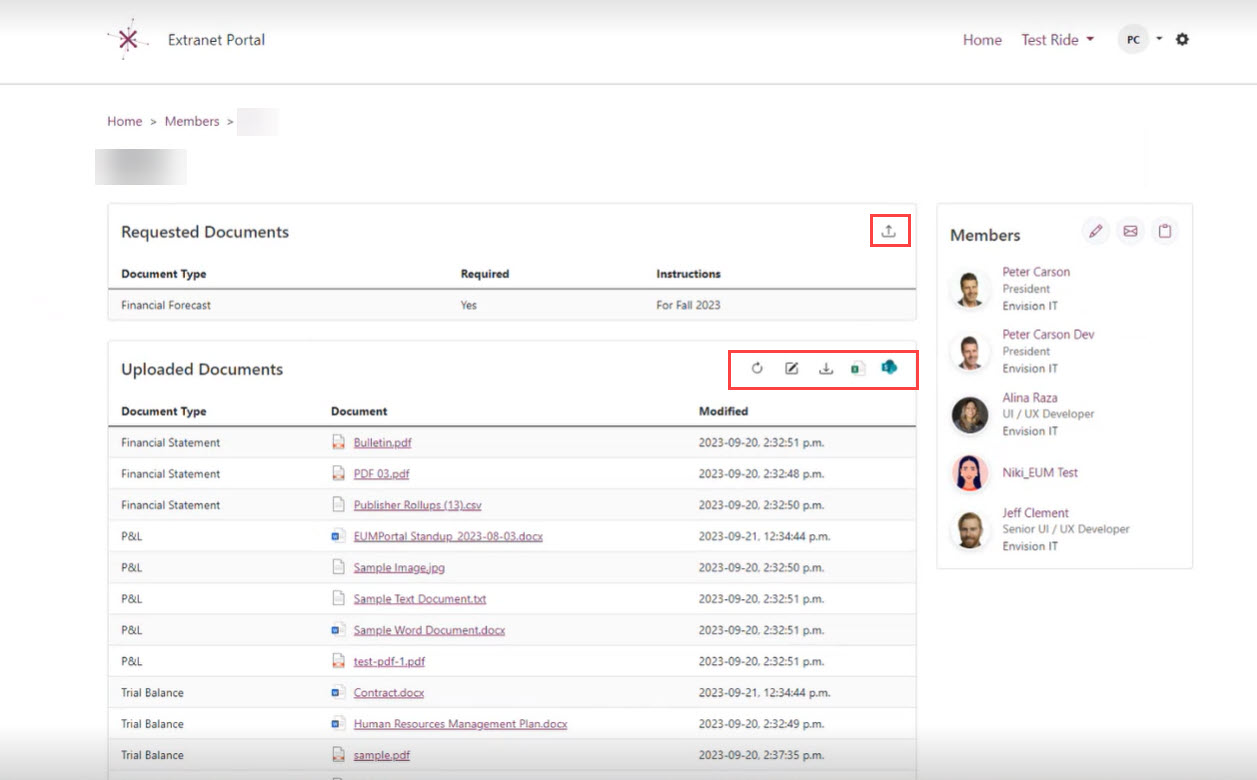
A notable feature of the data room is the panel for requested documents. Users view a list of documents that are requested to be uploaded as part of the data room functionality. Once the documents are uploaded, they become readily visible in a second panel designated for uploaded documents. Furthermore, the data room provides tools enabling users to update document metadata.
The screenshot below is a sample of how a Data Room can be used in the context of financial document exchange. Sensitivity labels can be applied to documents that are highly confidential, which will require users to go through Multi-Factor Authentication to access them.
Excel Tracking for Administrative Ease
Administrators can employ Excel tracking, a feature that allows them to specify or request documents from users. Continuing with EUM’s theme of simplifying Microsoft tools, Excel is utilized (a familiar tool to most business users) to ensure a smooth user journey. The Excel template within the Data Room is designed to be uncomplicated, allowing administrators to specify document types, requirements, and instructions seamlessly. Documents tagged as required within the Excel template will be displayed in the first panel of the Data Room interface.
Easy Document Upload and Metadata Tagging
Uploading a document is condensed into a straightforward process where users select a file from their desktop, optionally tag them (using tags specified in the Excel template), and click upload. This simplicity not only improves seamless adoption for users but also ensures accurate and consistent document management.
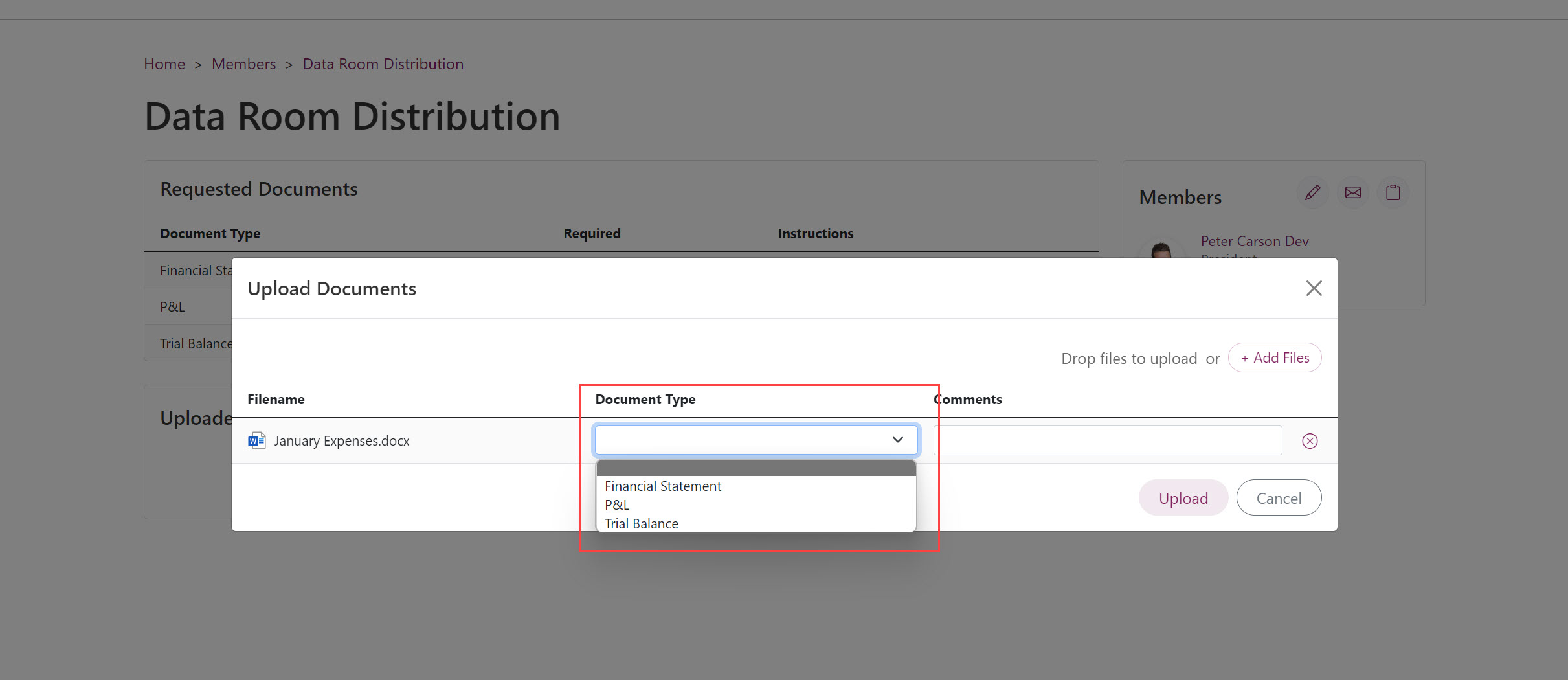
Easily customize tagging options and add comments to documents to provide context or additional details.
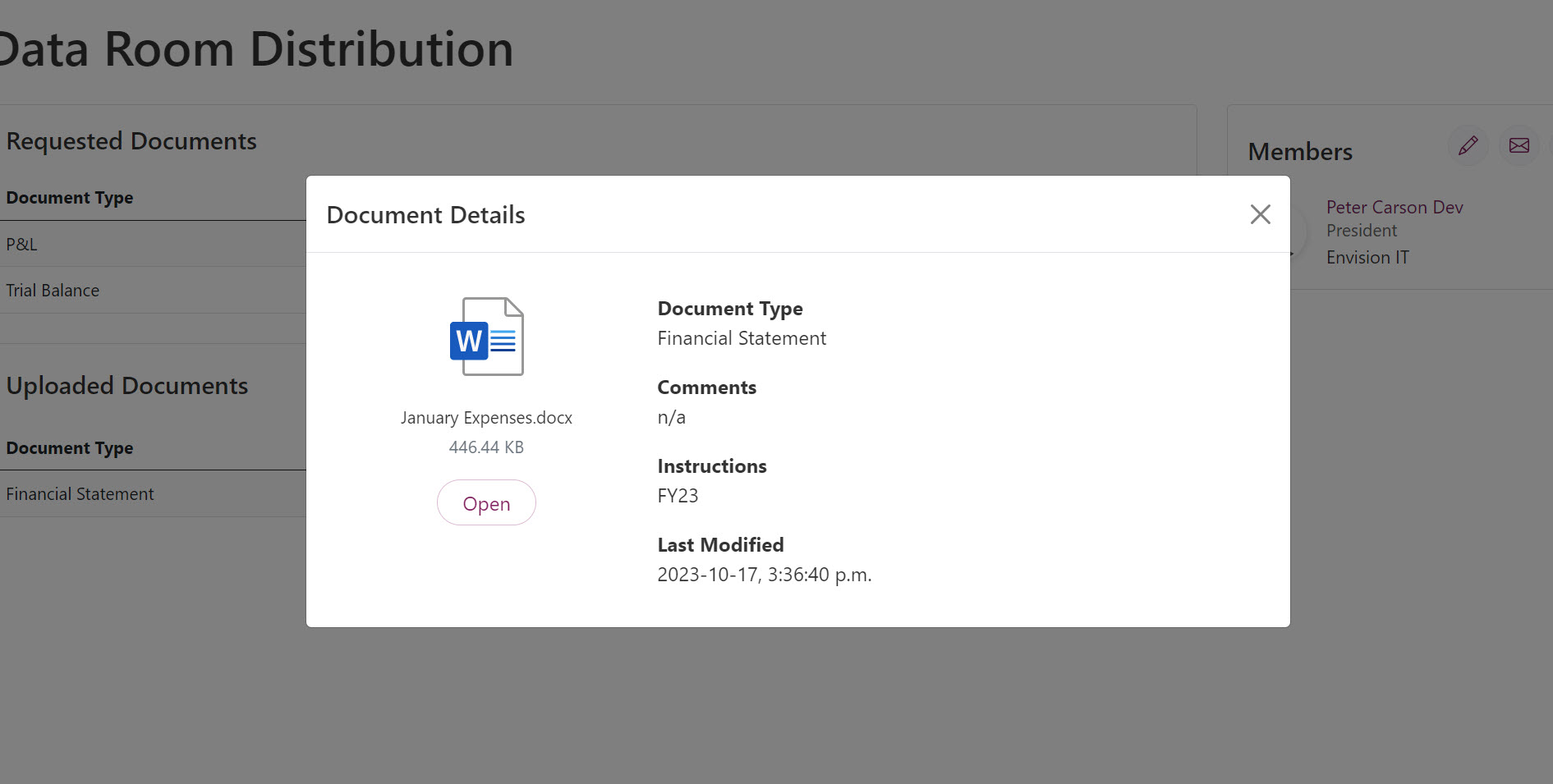
View metadata directly in Data Room without needing to open the file.
Document Download Capability
Following the document upload, administrators can re-enter the Data Room to download all the uploaded files. A collective downloading feature allows the administrators to download all documents in a zip file format, making it convenient to work with multiple documents simultaneously.
The EUM Data Room solution, from its simplified interface to its use of familiar tools like Excel and SharePoint Online, has been meticulously crafted to offer a secure, user-friendly, and effective environment for document management and sharing. This solution seamlessly intertwines security and usability, providing a platform where document exchange can be executed with minimal complexity, ensuring optimal user engagement, operational efficiency, and high security.